10 security issues
your business is facing
Helping businesses defend against cyber security misconfigurations.
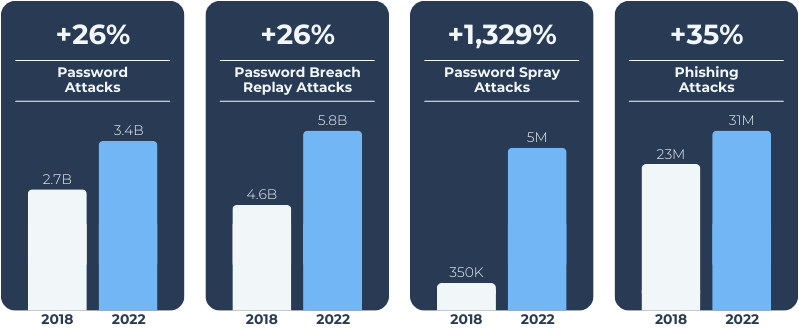
The National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) published research in October 2023 showing the top 10 cyber security misconfigurations found in large organisations, the report can be found here.
Enter your email below to download our take-home actions guide.

Trusted by:




Lighting the path of your Zero trust journey
The top 10 cyber security misconfigurations found in large organisations are:
- Bypass of system access controls
- Insufficient access control lists (ACLs) on network shares and services
- Poor credential hygiene
- Improper separation of user/administrator privilege
- Weak or misconfigured multifactor authentication (MFA) methods
- Default configurations of software and applications
- Poor patch management
- Unrestricted code execution
- Insufficient internal network monitoring
- Lack of network segmentation

Identity management #1
Bypass of system access controls
Based on our observations, this is a common event.
We often witness substantial efforts put into Entra ID and Active Directory security; however, access to alternative login methods remains open.
To address this issue, we recommend the following approaches:
- Employ GPO and Azure Policy to enforce a unified identity platform.
- Utilise SIEM to trigger alerts in response to any attempted bypass, including local logons.
- Continuously monitor for malicious logon attempts by means of SIEM.

Identity management #2
Insufficient access control lists (ACLs) on network shares and services
Maintaining oversight of share permissions and services can be incredibly difficult.
Therefore, our recommendation is to streamline the process and delegate responsibilities where feasible.
For our clients, we have implemented the following:
- Implement GPO and Azure Policy to establish a uniform identity platform.
- Leverage SIEM for immediate alerting in the event of any attempted bypass, including local logons.
- Employ SIEM for the ongoing monitoring of potentially malicious logon attempts.
Want to see the rest?
Download our quick take-home actions.
Identity management #3
Weak or misconfigured multifactor authentication (MFA) methods
Overly complex scoping of conditional access policies often gives rise to a common risk.
On occasion, we still come across configurations that apply per-user MFA, increasing the risk of accidental omissions.
Furthermore, this practice provides IT administrators with a simplified means to disable MFA while troubleshooting issues.


Identity management #4
Poor credential hygiene
Management of credential hygiene has been simplified thanks to Entra ID and Active Directory controls.
As a result, we are now observing more issues associated with assets that fall outside the purview of these systems, including local Windows and system accounts.
Our recommendations in this context are as follows:
- Adhere to the most current guidelines in Cyber Essentials for effective password management.
- Put in place measures to handle local system passwords or, preferably, eliminate local logons altogether. For mobile devices, enforce password controls using Mobile Device Management (MDM).
- Utilise data leakage controls to thwart the sharing of credentials among users and administrators through mediums like email and Teams.
- If your system is integrated with Entra ID B2C, consider the implementation of P2 licensing and the inclusion of risky sign-in management with automated remediation.
Identity management #5
Improper separation of user and administrator privilege
Consider the potential chaos that could ensue if one of your elevated accounts were to be exploited.
Fortunately, there are effective controls accessible to all.
Below, we've outlined some of these controls that we have implemented:
- Evaluate your teams and determine their essential rights, enabling elevation through Entra ID PIM. Consider shorter elevation windows for higher-level rights and establish regular access reviews to be managed by IT managers.
- Methodically transition your Azure resources into distinct subscriptions, optimising your PIM implementation. For instance, place network resources in a dedicated network subscription.
- Employ SIEM alerts to keep a vigilant eye on any attempts to circumvent the PIM system.

Software Maintenance, Configuration, Device Management #6
Default configurations of software and applications
Given our reliance on software and devices, effective large-scale management is crucial.
The following outlines the issues we've encountered and the resolutions we've implemented with our clients:
- Begin by ensuring the functionality of your inventory system. Subsequently, retain only necessary items and work towards decommissioning and consolidating wherever feasible.
- Implement only what you can effectively manage, and establish protective boundaries in your procurement and strategy. For instance, consider systems with Entra ID authentication to enable the use of SIEM and Entra ID security.
- Utilise Intune for deploying configurations to all mobile devices, whether they are for personal or business use.
- Leverage Intune to permit access to your services exclusively for compliant devices, a less commonly employed practice.
- Employ centralised configuration tools, including GPO and Azure Policy. In cases where a server is not domain-connected, opt for Intune.


Software Maintenance, Configuration, Device Management #7
Poor patch management
- Utilise Intune and Azure update services for swift environment patching and block or restrict outdated components.
- Whenever possible, limit your app selection to those available in the Microsoft Store to rely on its update mechanism.
- When introducing custom apps into your environment, make an effort to understand their update processes, such as custom scheduled tasks or registry settings.
Software Maintenance, Configuration, Device Management #8
Unrestricted code execution
- Utilise recommended security posture controls that can be delivered through Intune and GPO to limit code execution.
- Thoroughly review your anti-malware/anti-virus configuration and avoid assuming that it is fully deployed or configured to best practices.
- Install only the essential services, as attackers often exploit services like FTP and PowerShell.

Network Security #9
Insufficient internal network monitoring
Achieving this can be facilitated by utilising solutions like Azure Firewall or various Fortigate options for scrutinising internal network traffic. Additionally, we ensure that edge solutions, such as Azure WAF, direct incoming traffic through the internal firewall.
To monitor network traffic flows, you can employ Azure Network Watcher, setting up alerts for unusual activity or spikes. Furthermore, leverage Sentinel threat feeds to be notified of the detection of malicious actor IP addresses.
The Windows firewall, often an underappreciated resource, can be effectively utilised. We recommend collecting and retaining its logs for a brief period, especially for critical workloads. These logs can then be examined through Log Analytics or Sentinel for any security-related events.
Network Security #10
Lack of network segmentation
In Azure, streamlining network segregation through subnets, virtual networks, and network security groups is a more straightforward approach. Investing some initial effort is undoubtedly worthwhile to impede potential virus network propagation.
Limit outbound internet access through network rules, default gateway configurations, and local Windows (or third-party) firewalls.
Leverage Azure private peerings to minimise the reliance on internet breakout, which could potentially be exploited by viruses or data exfiltration systems.

Free limited scope audit
Any of the security issues mentioned
We can help you identify, remediate and govern any of the security issues mentioned.
