The adoption of Bring Your Own Device (BYOD) policies has become a prevalent trend in modern workplaces, providing employees with the flexibility to use their personal devices for work-related tasks. While BYOD offers numerous advantages, it also introduces security challenges that must be effectively addressed to safeguard corporate data.
This case study explores the journey of an anonymous client in improving data security by implementing BYOD policies and enhancing restrictions on devices accessing corporate data.
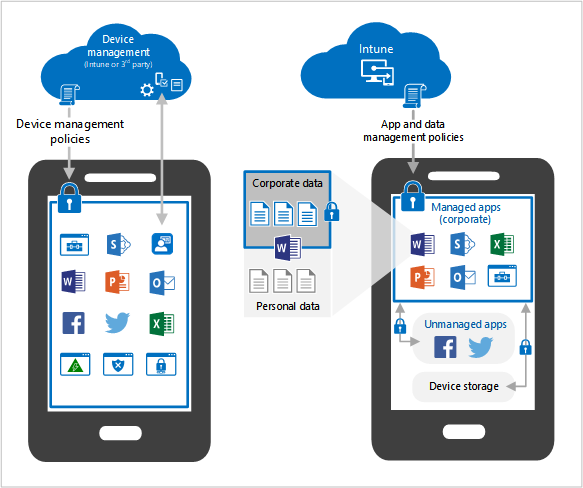
BYOD introduces specific challenges that organisations need to navigate for a successful implementation. The identified challenges for our client were:
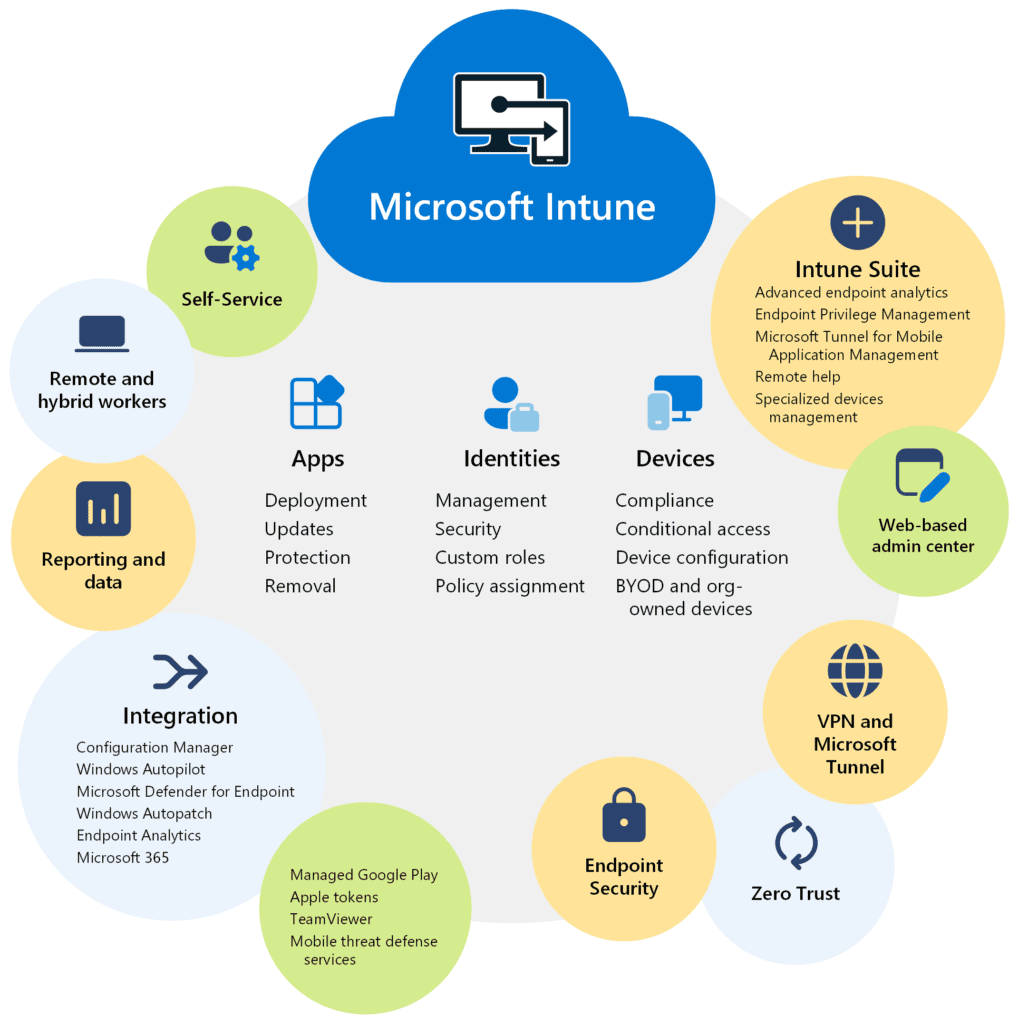
To address these challenges, the client opted for Microsoft Intune (used to be Endpoint Manager) BYOD policies, leveraging its capabilities to enhance security on personally owned devices accessing corporate data. The implemented solution included:
The implementation of Intune BYOD policies yielded significant benefits for the client:
Please visit Microsoft’s website for more Intune benefits: https://learn.microsoft.com/en-us/mem/intune/fundamentals/what-is-intune
Due to the sensitive nature of this project, the client’s details are kept confidential. Discussions with the client can be arranged with their agreement.
“The flexibility offered by BYOD has empowered our employees, allowing them to use their preferred devices for work-related tasks. This not only aligns with the modern work culture but has also significantly enhanced employee satisfaction and engagement.”
This case study demonstrates how a strategic implementation of BYOD policies, specifically using Microsoft Intune, can effectively address the challenges posed by the integration of personal devices in the workplace. The client’s commitment to enhancing data security while maintaining a positive user experience showcases the success of a well-thought-out BYOD strategy.
BYOD stands for “Bring Your Own Device,” a policy that allows employees to use their personal devices, such as smartphones, tablets, and laptops, for work purposes.
Intune BYOD policies refer to the rules and configurations set in Microsoft Intune, a cloud-based service that manages devices and applications to ensure security and compliance for personal devices used within an organisation.
Challenges include ensuring data security, maintaining compliance with regulatory standards, managing diverse devices, and protecting against potential threats from unsecured personal devices.
Microsoft Intune BYOD policies enhance security by enforcing encryption, requiring secure passwords, enabling remote wipe capabilities, and ensuring that only compliant devices can access corporate resources.
Benefits include centralised device management, improved security compliance, seamless integration with other Microsoft services, and enhanced productivity by allowing employees to use familiar devices.

To see the wide range of projects we’ve worked on, click here to read other case studies.